Charming Kitten exposed: spy unit led Iran’s surveillance for deadly plots

A covert unit of cyber agents is at the forefront of Iranian efforts to surveil perceived enemies and was behind failed bids to kill Israelis in Turkey, leaked documents obtained by Iran International and an informed source revealed.
“Department 40”, whose existence, structure and personnel were first reported by Iran International, is a creation of the Islamic Revolutionary Guard Corps’ counterintelligence unit.
In the boldest foreign operation which can be attributed to the group, its personnel gathered information used in an alleged plot to kill Israeli citizens including the former consul and his partner in Istanbul in 2022. Iran flatly denies any role.
Other activities relate to pursuing kamikaze drones to attack Israel, analyzing drone footage of the UK embassy in Tehran and attempts to penetrate security databases in the United Arab Emirates.
The materials reviewed by Iran International show Department 40 accessed the location, contacts and communications of Iranian citizens and foreigners, collating the purloined information into a vast database accessible to superiors in the Revolutionary Guards.
Targets included journalists, dissidents, foreign staff of embassies in Tehran and employees of foreign governments and companies.
Its activities, the documents showed, succeeded in infiltrating databases of foreign official and non-governmental bodies, including the Abu Dhabi and Fujairah police in the United Arab Emirates, FlyDubai and EgyptAir airlines, the municipality of a mid-sized city in Jordan as well as similar institutions in Turkey and Saudi Arabia.
The authorities and entities mentioned in the documents did not immediately respond to Iran International requests for comment.
Before Iran International’s report on Thursday, some of the documents on Department 40 were anonymously leaked online on GitHub, a platform for coders.
The origin of that submission was not immediately clear.
Until now, it was believed that the activities of the department—widely referred to as Charming Kitten in the intelligence and cybersecurity community—was limited to phishing activities.
But progress reports and internal communications compiled by its personnel demonstrated broader capabilities including hacking, extracting data from devices of targeted entities and their compilation in a database called Kashef, or Revealer.
Using Kashef, an authorized agent can quickly identify individuals connected to persons of interest by referencing their mobile phone call records, flight history or geolocation data.
A review of the identities of about 60 Department 40 agents showed that many have recruited members of their own families and concealed their activities behind multiple layers of front companies.
Various cybersecurity companies had previously identified the Department’s activities in neighboring countries as well as in Israel and Europe but its identity had not emerged publicly.
Among the activities directed at Iran’s Mideast arch-nemesis, Department 40 posted fake job ads to spy for Israel inside Iran to root out potential collaborators as well as setting up Telegram groups organizing protests against Prime Minister Benjamin Netanyahu.

Pistols, silencers
The Department’s most ambitious operation, according to the source familiar with the matter and corroborated by aspects of the body’s stated duties detailed in the documents, related to the alleged deadly attempt on Israelis in Istanbul in 2022.
According to the source, Department 40 assisted the IRGC counterintelligence organization called Unit 1500 in gathering information used in the failed bid to assassinate Israeli tourists and the former Israeli consul Yosef Levi Sfari and his partner in Istanbul.
Organizational documents and intelligence reports from Department 40 list among its priorities “the collection of intelligence for assassination operations” and other materials describe seeking to kill Israelis with drones.
They did not specifically refer to the alleged assassination attempts in Turkey.
Israel’s intelligence service, alarmed by what it saw as an imminent Iran-backed attack, instructed its citizens in Istanbul on June 17 to lock themselves inside or immediately flee the country.
Turkish authorities, according to domestic media reports, arrested five Iranian citizens implicated in the foiled plot and confiscated two pistols and silencers.
The spy drama had followed the unexplained assassination of IRGC Colonel Sayad Khodai in Tehran by armed assailants the previous month which Tehran blamed on Israel, vowing revenge.
It came just as the Jewish State and Turkey explored a rare rapprochement, and Israel’s foreign minister at the time Yair Lapid blamed Tehran.
“Iran is behind these attempted terrorist attacks. The intelligence leaves no doubt about it. We’re not only talking about the murder of innocent Israeli tourists, but also a clear violation of Turkish sovereignty by Iranian terror."
For its part, Iran flatly denied the allegations, with then-foreign ministry spokesman Saeed Khatibzadeh calling Lapid’s assertion “ridiculous” and a “pre-designed scenario to destroy relations between the two Muslim countries".
'Brothers and sisters'
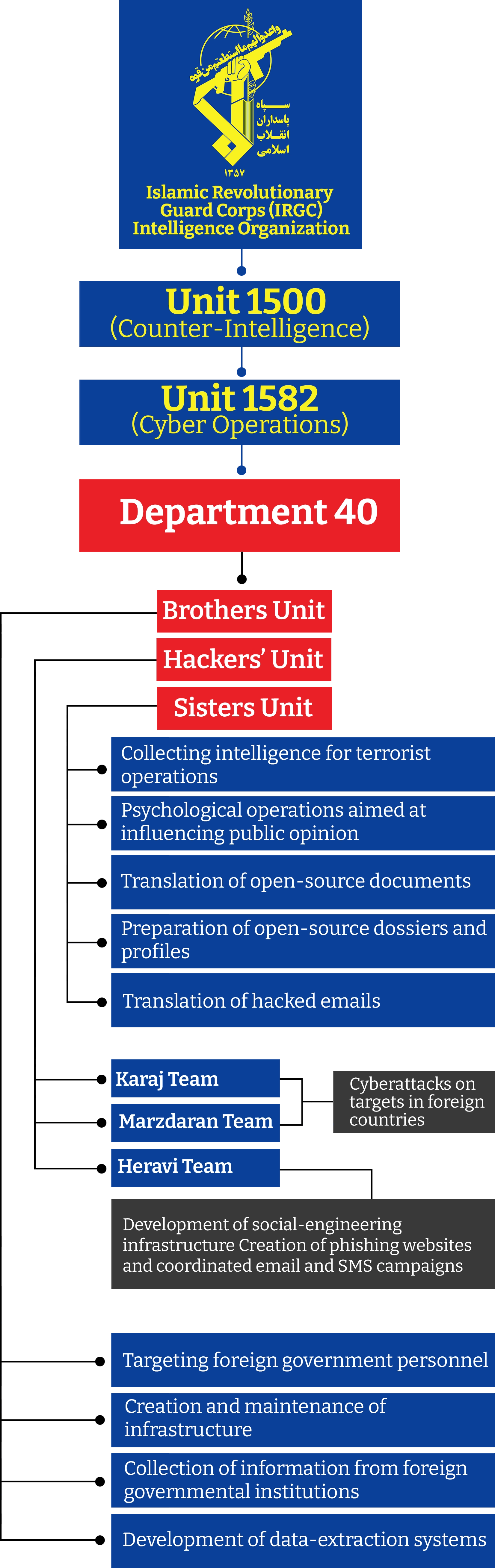
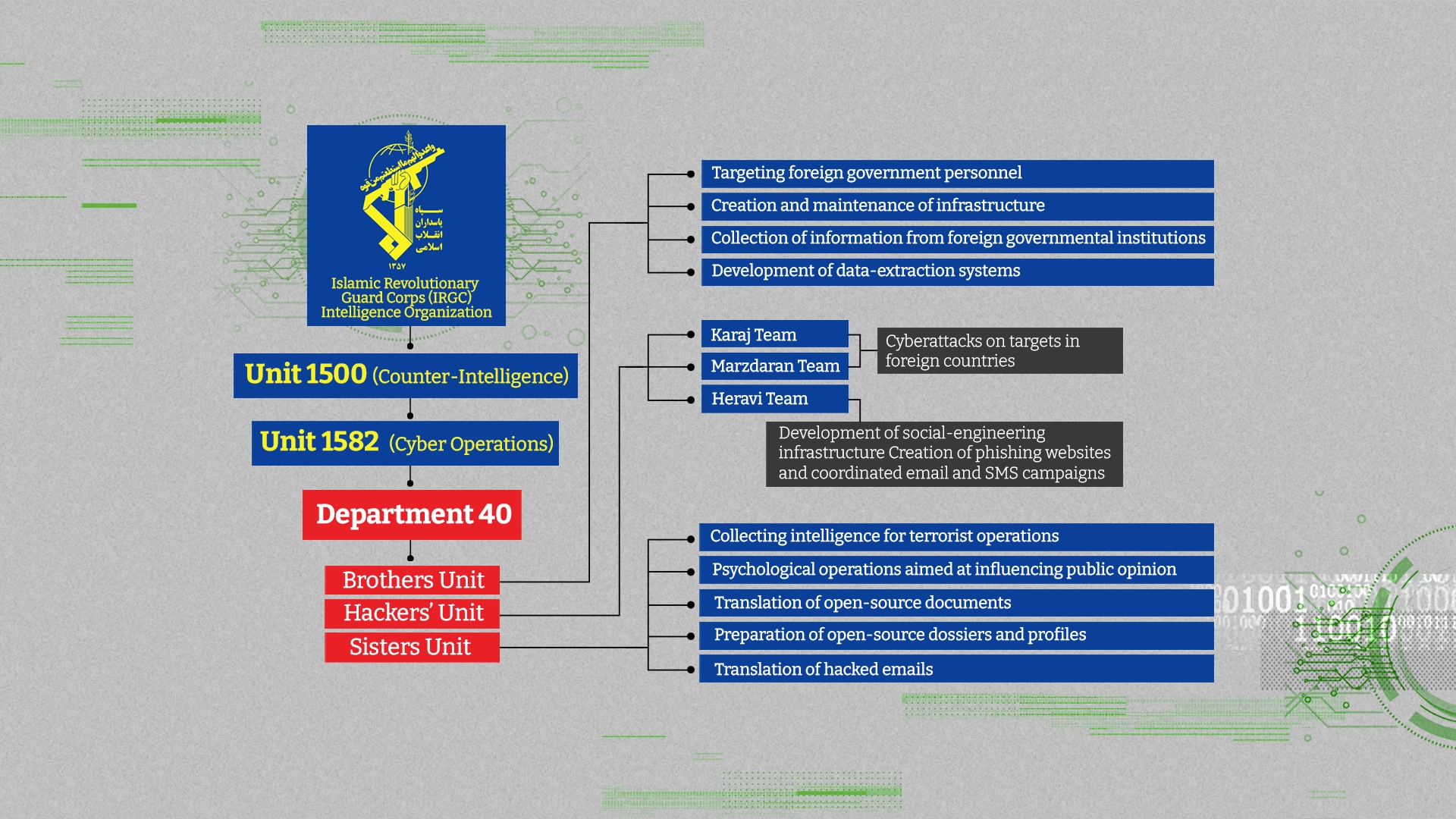
Department 40, the documents show, is composed of three sub-units: a group of hackers, the Brothers, and the Sisters. In the Islamic Republic, the titles ‘Brothers' and 'Sisters’ are common institutional terms for men and women.
The Brothers unit, according to organizational charts contained in the leaked documents, is responsible for, among other duties, “targeting foreign government personnel” and “collection of information from foreign governmental institutions.”
For their part, the Sisters unit is tasked with “the collection of intelligence for assassination operations” and “psychological operations aimed at influencing public opinion.”
The hacking teams carry out “cyberattacks on targets in foreign countries and oversee “the creation of phishing websites and coordinated email and SMS campaigns.”
The leaked documents reviewed by Iran International indicate Department 40 orchestrated many of the cyber operations which security experts and watchdogs had attributed generally to Iran-linked groups in recent years.
Prominent among them are so-called “spy-ads” appearing on some VPN services used by Iranians to bypass state censorship of the internet which invite users to collaborate with Israel.
The documents reviewed by Iran International show that all internet domains associated with a network overseeing the ads—known as VIP Human Solution—belonged to Department 40, and aimed to entrap potential spies.
The Revealer
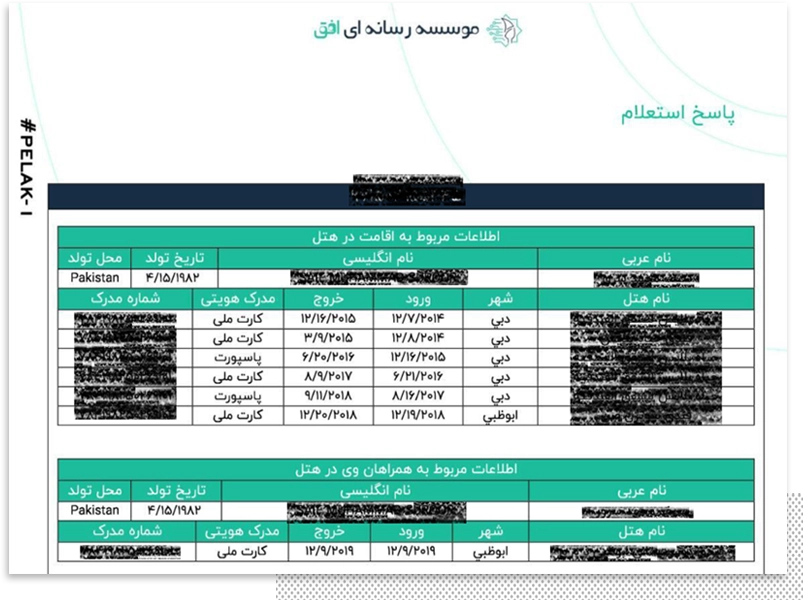
The Kashef (Revealer) database appears to be Department 40’s core project, and the leaked materials include a video showing a confidential presentation of Version 3 of the platform, which became operational in June 2022.
It reveals the extent and type of information accessible there, including Iranians’ phone numbers, records of phone calls and text message, social media activities, home and workplace addresses and movement patterns.
Cybersecurity analyst Nariman Gharib told Iran International that the databases obtained by hackers affiliated with Department 40 are transferred into Kashef to allow agents to track and catalogue information about their selected targets.
“The system allows the unit to build intelligence files for conducting physical attacks against these targets,” Gharib said. “This is a cyber capability designed to support assassination operations.”
The precise goal of the department's information-gathering on people and entities was often not clear, and did not appear in many cases to intend physical harm.
The Kashef system contained meticulous information on Iranian dual-nationals, embassy staff, employees of foreign-linked companies, and journalists.
The platform, according to the documents, aims to facilitate overseas operations by the Intelligence Ministry and the IRGC external operations branch, the Quds Force.
It maps connections of persons and sites of interest. If two phone numbers of interest show up in one location, the system alerts the agents
For years, dual-national Iranians traveling to Iran were required to fill out forms that asked their emails and social media accounts.
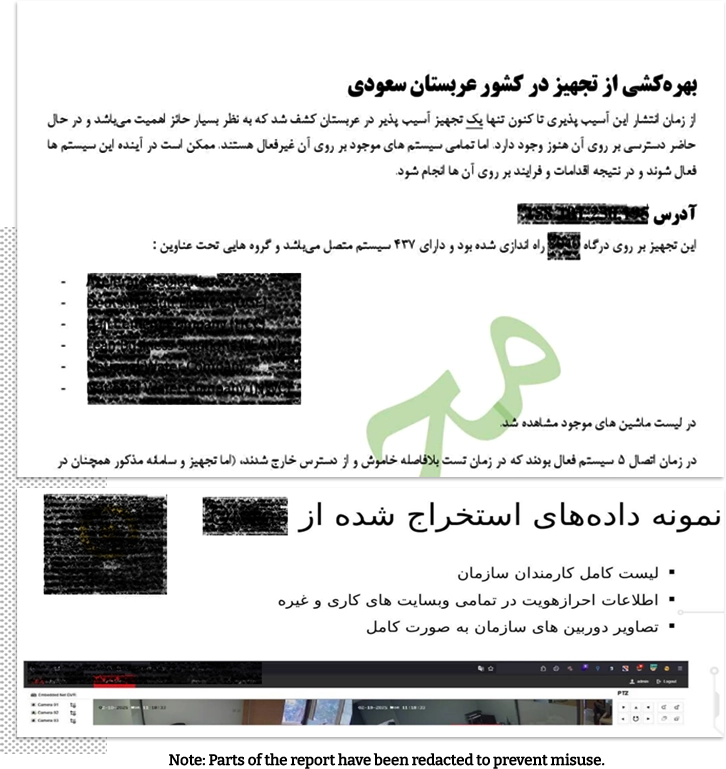
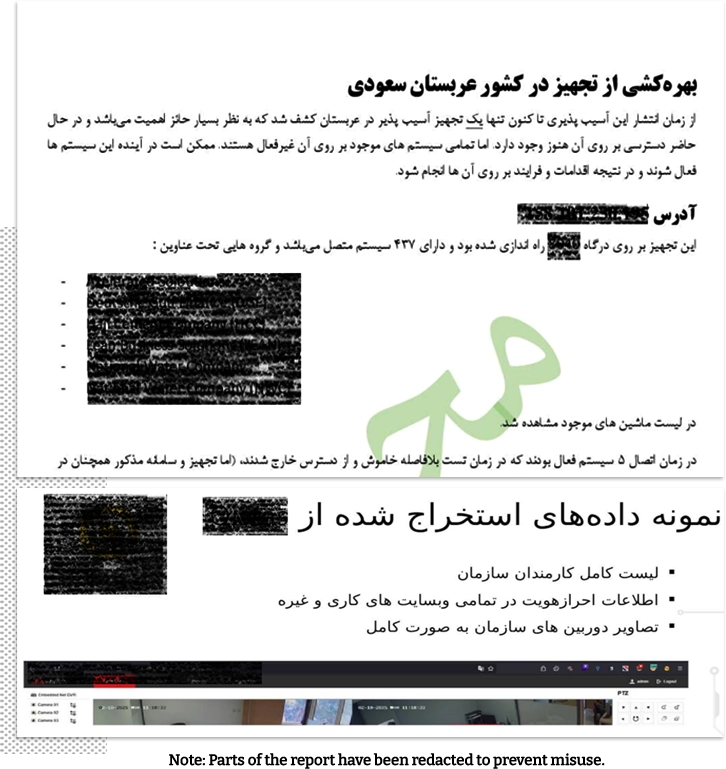
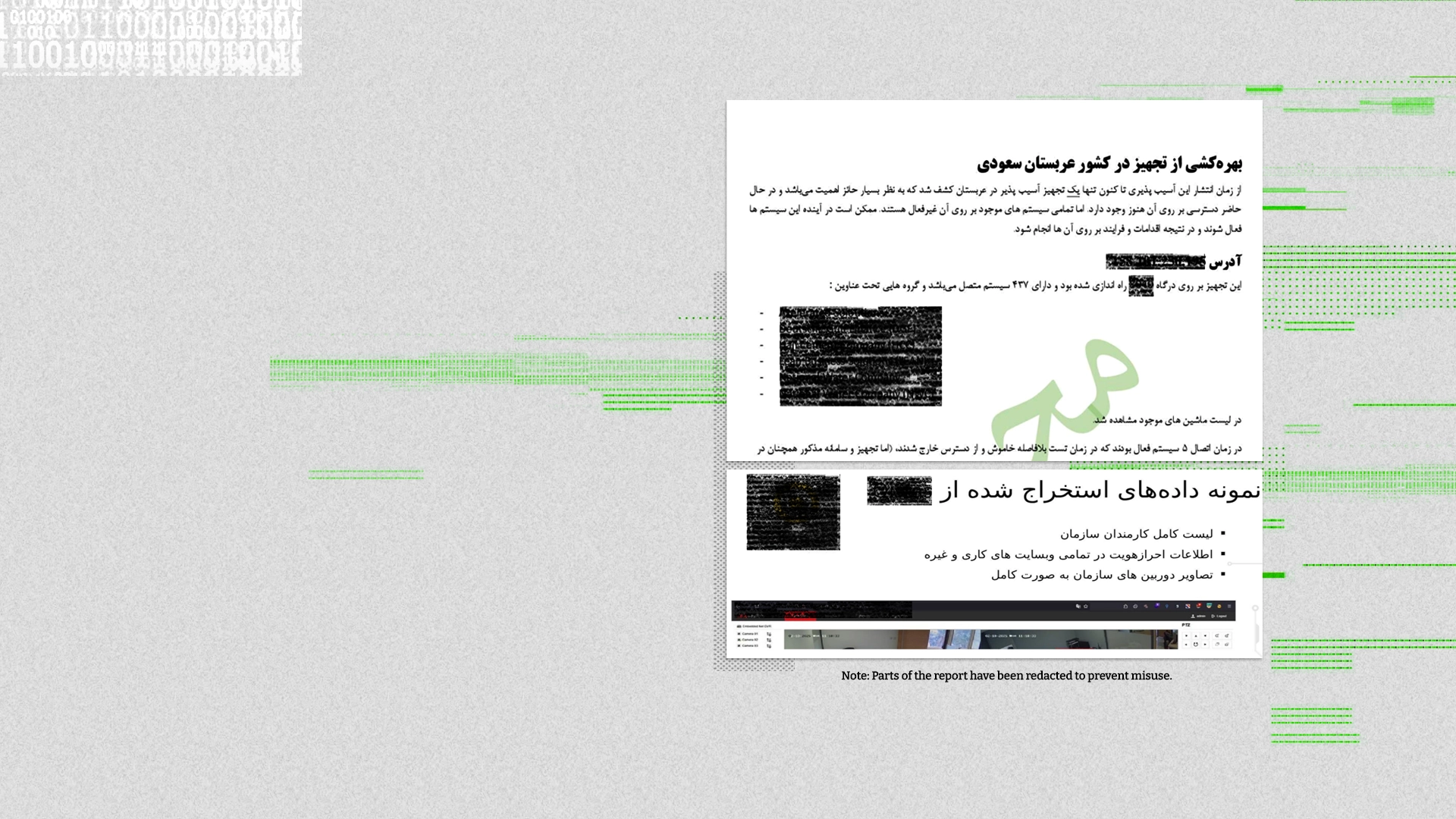
Confidential internal reports from Department 40 reviewed by Iran International reveal that its cyberattacks gained access to foreign state and private institutions such as the Abu Dhabi and Fujairah police, FlyDubai, EgyptAir, Azerbaijan’s SOCAR energy holding, and the Russeifa municipality in northern Jordan from which data on targeted individuals could be collected.
Where data could not be obtained directly, the unit would venture other means.
One Department 40 report reviewed by Iran International shows that after an initial failure to access police records in the United Arab Emirates, the hackers targeted a contractor firm working with the police.
Brothers and sisters
Department 40, the documents show, is composed of three sub-units: a group of hackers as well as the so-called Brothers and an all-female unit, the Sisters.
The Brothers unit, according to organizational charts contained in the leaked documents, is responsible for, among other duties, “targeting foreign government personnel” and “collection of information from foreign governmental institutions.”
For their part, the Sisters unit is tasked with “the collection of intelligence for assassination operations” and “psychological operations aimed at influencing public opinion.”
The hacking teams carry out “cyberattacks on targets in foreign countries and oversee “the creation of phishing websites and coordinated email and SMS campaigns.”
The leaked documents reviewed by Iran International indicate Department 40 orchestrated many of the cyber operations which security experts and watchdogs had attributed generally to Iran-linked groups in recent years.
Prominent among them are so-called “spy-ads” appearing on some VPN services used by Iranians to bypass state censorship of the internet which invite users to collaborate with Israel.
The documents reviewed by Iran International show that all internet domains associated with a network overseeing the ads—known as VIP Human Solution—belonged to Department 40, and aimed to entrap potential spies.
The Revealer
The Kashef (Revealer) database appears to be Department 40’s core project, and the leaked materials include a video showing a confidential presentation of Version 3 of the platform, which became operational in June 2022.
It reveals the extent and type of information accessible there, including Iranians’ phone numbers, records of phone calls and text message, social media activities, home and workplace addresses and movement patterns.
Cybersecurity analyst Nariman Gharib told Iran International that the databases obtained by hackers affiliated with Department 40 are transferred into Kashef to allow agents to track and catalogue information about their selected targets.
“The system allows the unit to build intelligence files for conducting physical attacks against these targets,” Gharib said. “This is a cyber capability designed to support assassination operations.”
The precise goal of the department's information-gathering on people and entities was often not clear, and did not appear in many cases to intend physical harm.
The Kashef system contained meticulous information on Iranian dual-nationals, embassy staff, employees of foreign-linked companies, and journalists.
The platform, according to the documents, aims to facilitate overseas operations by the Intelligence Ministry and the IRGC external operations branch, the Quds Force.
It maps connections of persons and sites of interest. If two phone numbers of interest show up in one location, the system alerts the agents
For years, dual-national Iranians traveling to Iran were required to fill out forms that asked their emails and social media accounts.
Confidential internal reports from Department 40 reviewed by Iran International reveal that its cyberattacks gained access to foreign state and private institutions such as the Abu Dhabi and Fujairah police, FlyDubai, EgyptAir, Azerbaijan’s SOCAR energy holding, and the Russeifa municipality in northern Jordan from which data on targeted individuals could be collected.
Where data could not be obtained directly, the unit would venture other means.
One Department 40 report reviewed by Iran International shows that after an initial failure to access police records in the United Arab Emirates, the hackers targeted a contractor firm working with the police.

Key figures
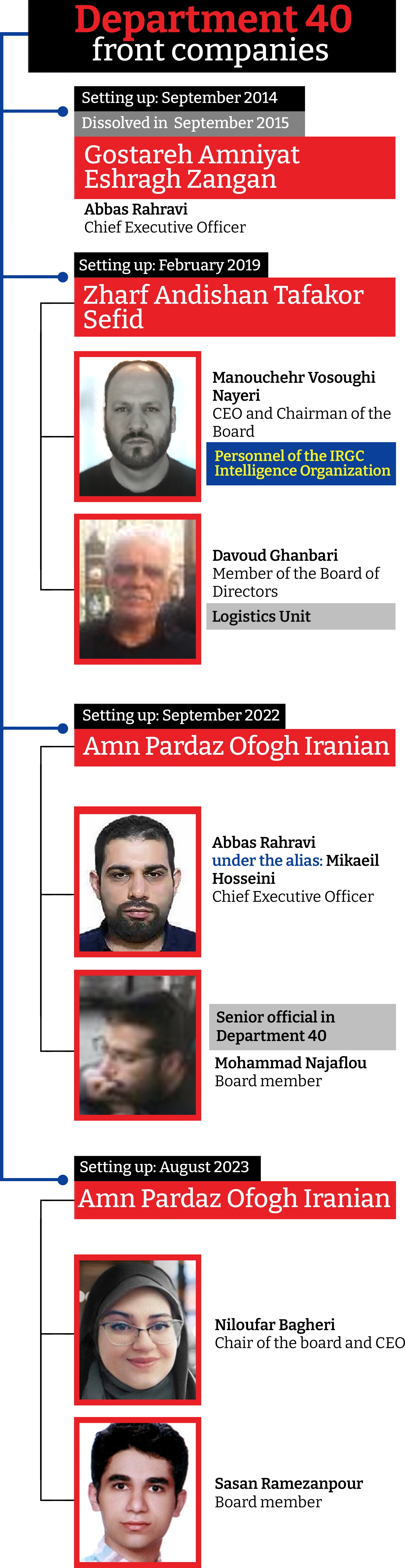
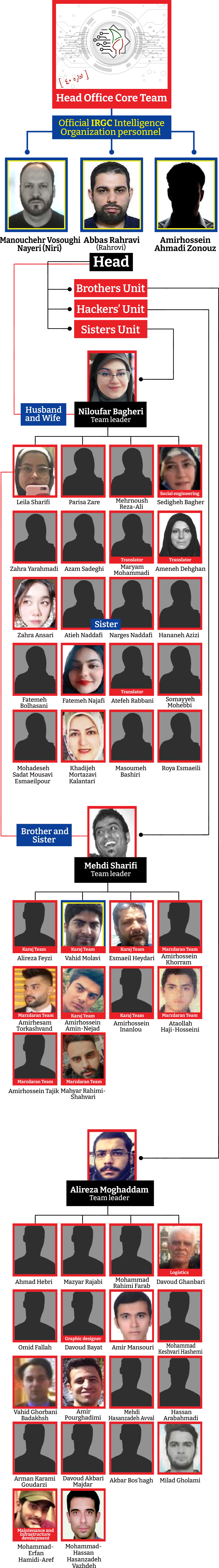
The leader of Department 40 is Abbas Rahravi, 33, from Zanjan in northwest Iran, who also operates under aliases Mikaeil Hosseini and Abbas Hosseini.
Two other IRGC intelligence officers, Manouchehr Vosoughi Nayyeri and Amirhossein Ahmadi Zonouz, are key leaders in the unit.
The informed source who spoke to Iran International assessed that Department 40 in its current form was set up in the first half of the last decade with the limited mission of launching cyber operations.
The unit operates as a department under Unit 1582, the cyber-operations bureau, which is itself a subdivision of Unit 1500 of the IRGC Intelligence Organization.
Ruhollah Bazghandi, the IRGC’s former deputy counterintelligence chief and former head of Unit 1500, played a direct role in establishing the Unit, the documents showed.
The documents reviewed by Iran International show that the unit’s activities now extend well beyond its original mandate.


Front companies
Department 40 operatives formally work as employees of three front companies. Rahravi runs two with the help of his wife—who also heads the Sisters unit.
The third is overseen by Vosoughi Nayyeri and another member of the Brothers team. The entities have been registered as service companies offering website design or management consulting.
Personnel are based at six locations in and around Tehran or work remotely, the documents indicate. One site is the defunct Martyrs Base military facility in east Tehran, which is also the registered address of the Zharf Andishan Sefid Institute, one of Department 40’s front companies.
They also work out of facilities in the northern Iranian city of Qom, in Karaj outside the capital and another two in central and western Tehran.
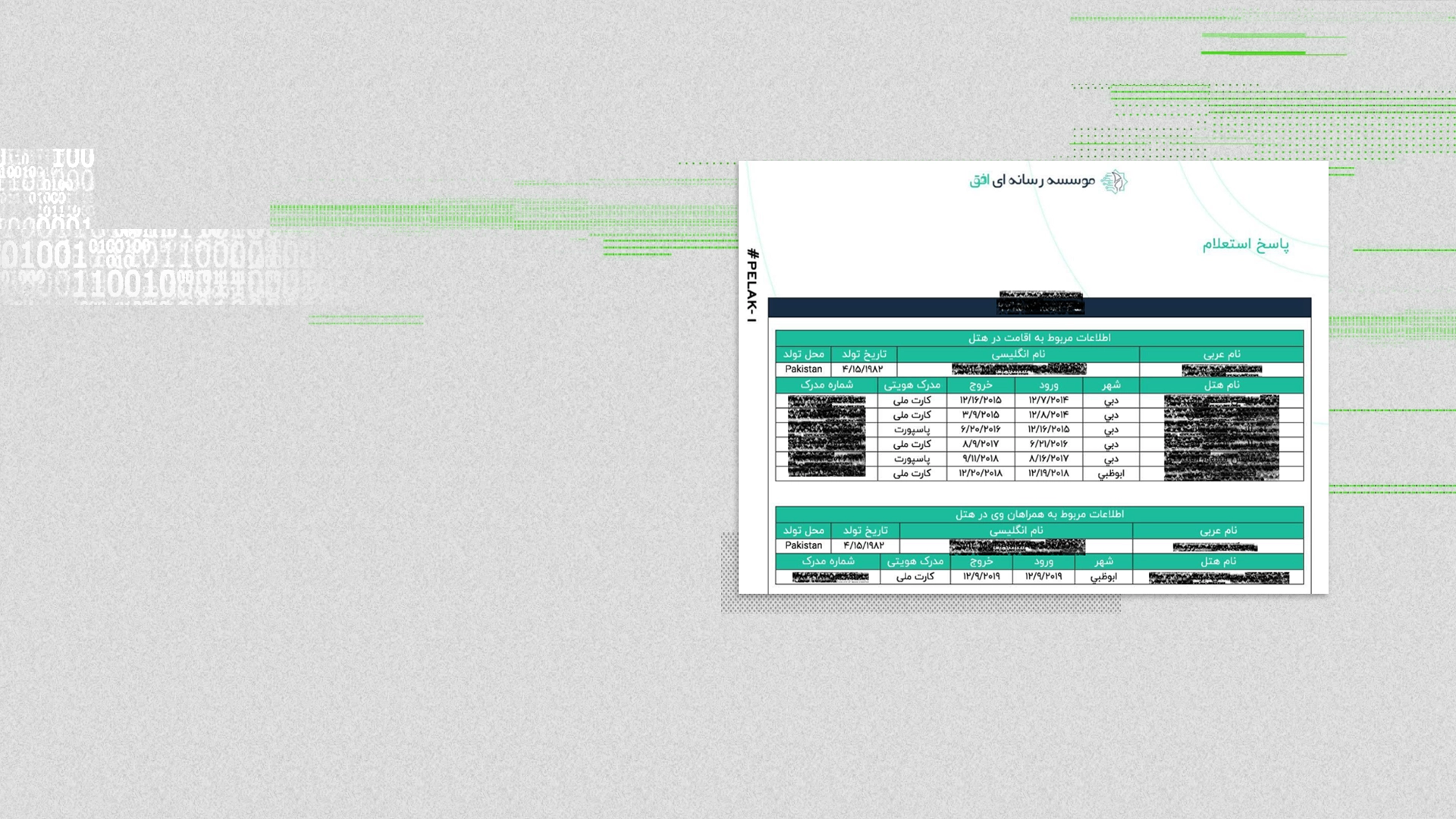
According to surveillance and monitoring of the area surrounding the company, on Sunday, 12/18/2022 at 09:40, a veiled woman wearing a chador and face covering entered the alley. After checking the surroundings and making sure no pedestrians were present, she proceeded to write slogans on the wall at the end of the alley.
On Sunday, 12/25/2022 at 09:41, the same woman, wearing the same clothing, entered the alley again and noticed that her previous graffiti had been removed. After examining the area and ensuring no one was around, she repeated the wall-writing.
Following an alert from the monitoring system and subsequent surveillance, she eventually entered a residence at No. *********************** Street. Upon checking the location, it was observed that around the same time, several other women with similar attire also entered the same building. It is likely that, given the matching day and hour, a women's gathering was being held at that location, or the premises may have been used as a safe house for team activities.

Overseas recruitment
Department 40, the documents show, created a website called “Tecret” to recruit and hire cyber specialists in Israel, Turkey and the United Arab Emirates.
The site claims to belong to a company of the same name, but the informed source told Iran International that no such company is registered in the Emirates.
According to the source, Department 40 operatives use the website to attempt to recruit cyber experts in the three countries.
“Individuals linked to Department 40 have tried to establish contact with various people abroad and deceive them into harming those countries or recruit them as intelligence assets,” the source said.
They have also used a platform called Gulf Security in an effort to recruit employees in the Emirati security sector to gain access security networks there.
Department 40 has extracted data from state and private institutions in Israel, Turkey, Saudi Arabia, Kuwait, Egypt, Jordan, Azerbaijan, India, Afghanistan and the United Arab Emirates, the documents indicated.
Among the targeted jurisdictions are states with good ties with Tehran like Oman and even faraway countries like Singapore.
Department 40 compiled profiles on non-Iranian citizens and Iranian dual nationals, with documents describing attempts to access the email accounts of some of the targeted individuals, though whether the efforts succeeded is unclear.
Among them are prominent dissidents, vocal opponents of the Islamic Republic and individuals linked with international affairs concerning Iran.
Iran International can reveal a few names to have been targeted in this operation. There was no indication that department ultimately intended them any harm, and they did not immediately respond to requests for comment.
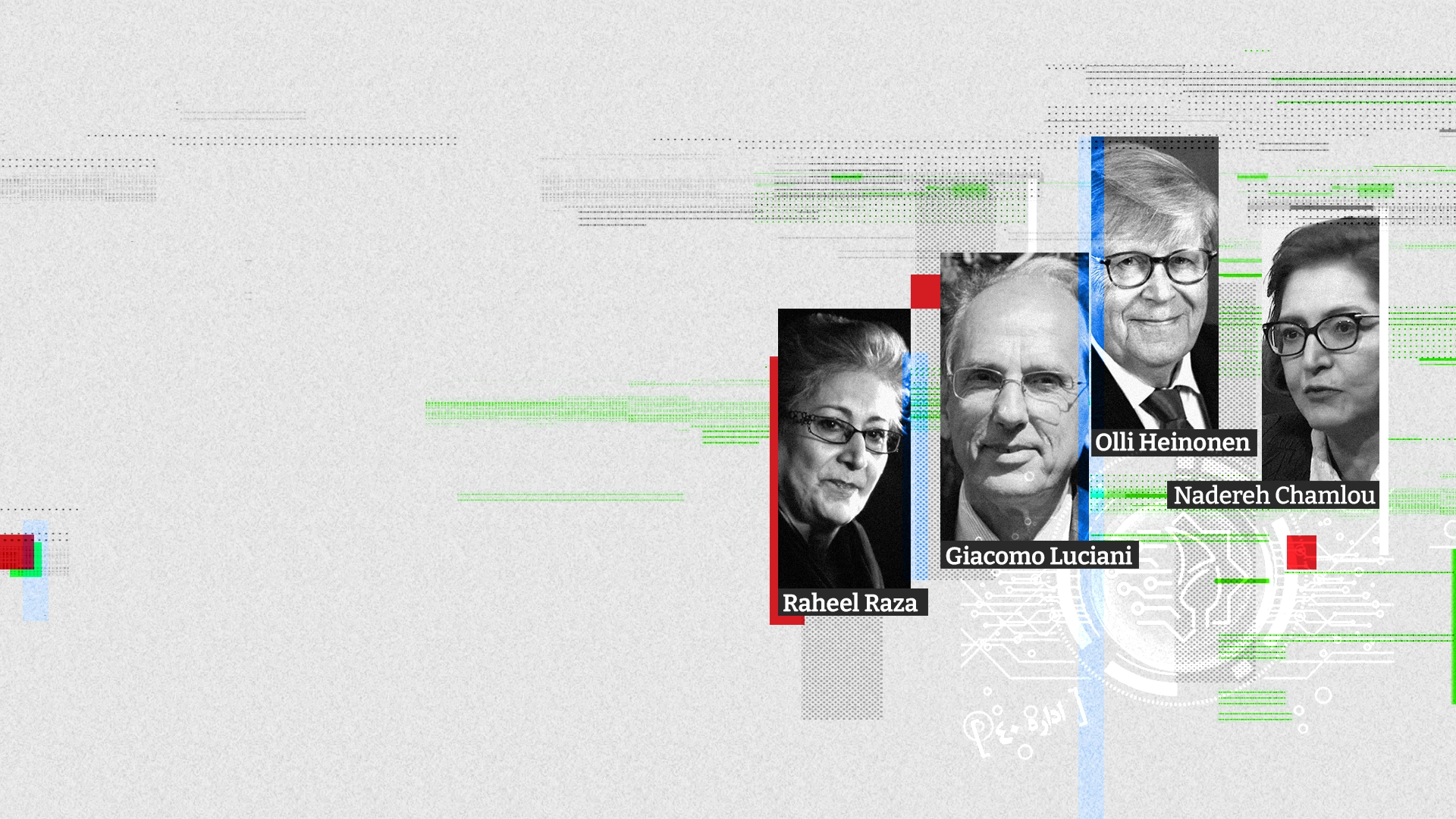
They include Olli Heinonen, former deputy director general of the International Atomic Energy Agency (IAEA) for Safeguards, who worked on the Iran dossier for the UN nuclear watchdog.
Another is Giacomo Luciani, a prominent researcher on the political economy of energy in the Persian Gulf, who has played an important role in shaping EU-Persian Gulf energy relations.
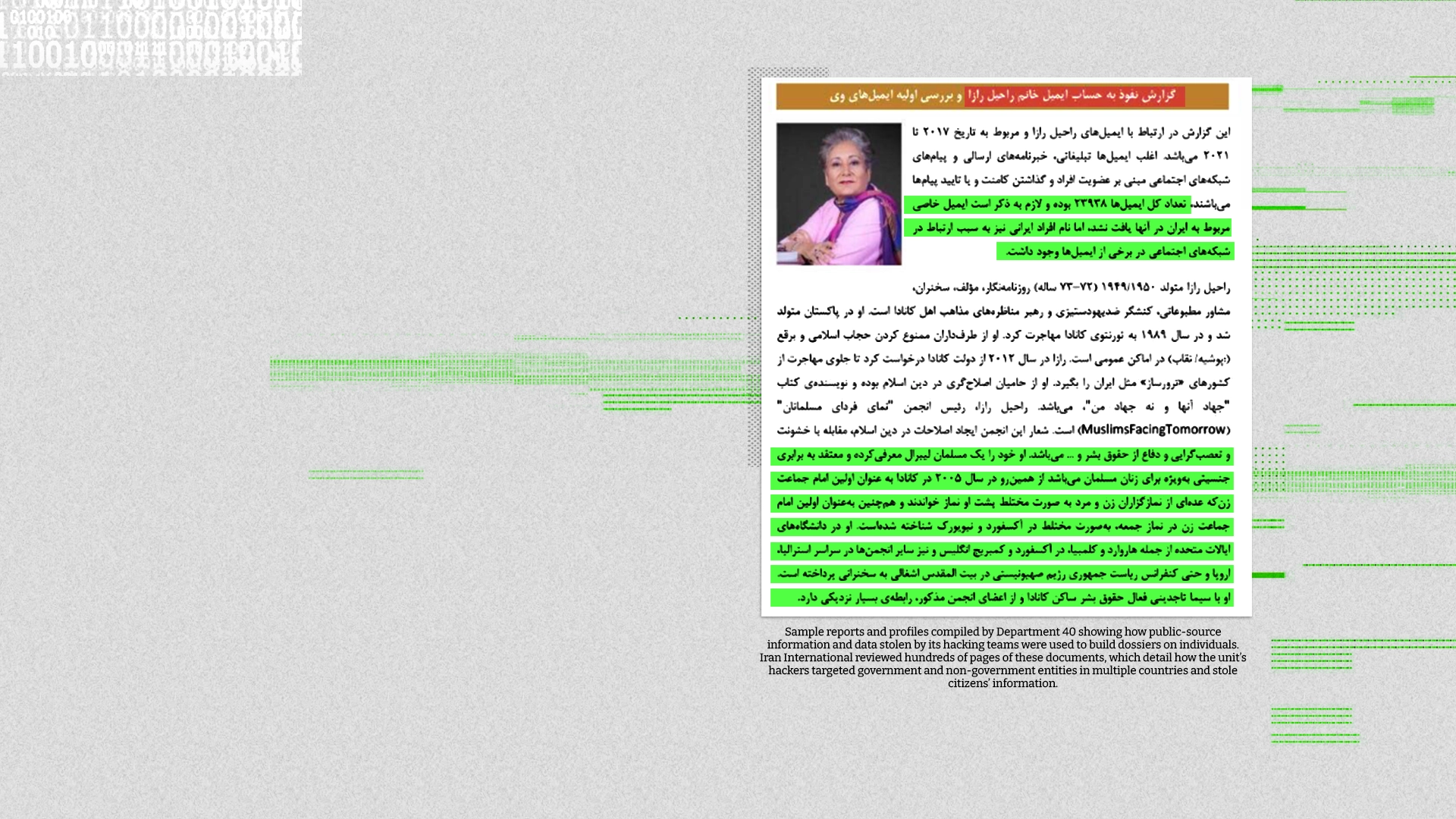
Raheel Raza, a Canadian journalist of Pakistani origin, known for extensive activism against “Islamic terrorism,” was also scrutinized, along with Nadereh Chamlou, a former senior adviser at the World Bank and a non-resident senior fellow at the Atlantic Council.
Additionally, a Department 40 report described Iranian-Swedish dual national Reza Neshat, branding him “anti-system.”
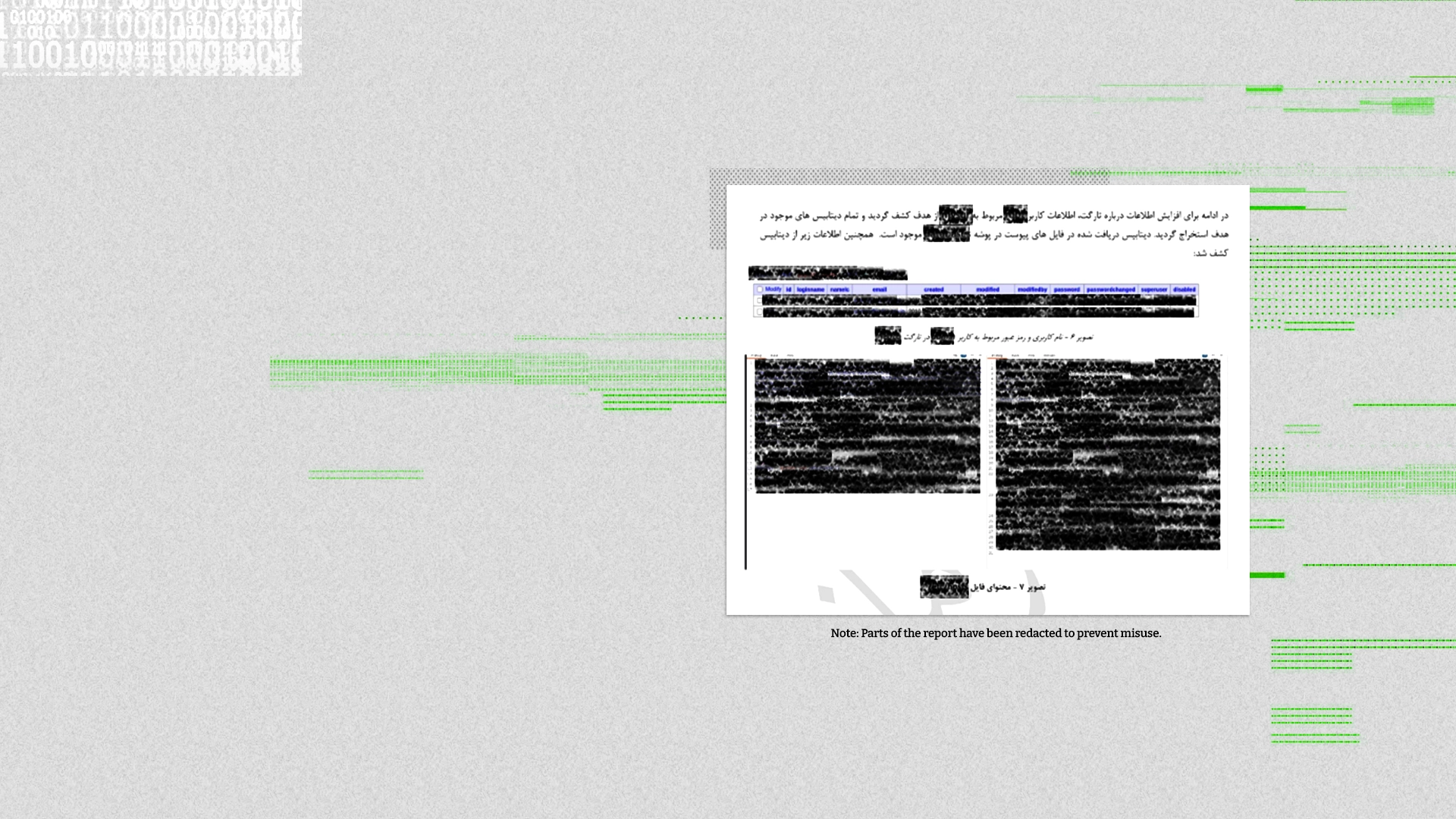
One report from Department 40 reviewed by Iran International described the hacking of a non-Iranian citizen’s email accounts.
In it, the author describes emails found in the person's inbox and explains to senior officials how many of them involve Iranian or dual-national individuals and how those individuals could become new targets for scrutiny.
After gaining access to the person’s emails, they investigated their contacts and explored leads to identify subsequent targets.




Overseas recruitment
Department 40, the documents show, created a website called “Tecret” to recruit and hire cyber specialists in Israel, Turkey and the United Arab Emirates.
The site claims to belong to a company of the same name, but the informed source told Iran International that no such company is registered in the Emirates.
According to the source, Department 40 operatives use the website to attempt to recruit cyber experts in the three countries.
“Individuals linked to Department 40 have tried to establish contact with various people abroad and deceive them into harming those countries or recruit them as intelligence assets,” the source said.
They have also used a platform called Gulf Security in an effort to recruit employees in the Emirati security sector to gain access security networks there.
Department 40 has extracted data from state and private institutions in Israel, Turkey, Saudi Arabia, Kuwait, Egypt, Jordan, Azerbaijan, India, Afghanistan and the United Arab Emirates, the documents indicated.
Among the targeted jurisdictions are states with good ties with Tehran like Oman and even faraway countries like Singapore.
Department 40 compiled profiles on non-Iranian citizens and Iranian dual nationals, with documents describing attempts to access the email accounts of some of the targeted individuals, though whether the efforts succeeded is unclear.
Among them are prominent dissidents, vocal opponents of the Islamic Republic and individuals linked with international affairs concerning Iran.
Iran International can reveal a few names to have been targeted in this operation. There was no indication that department ultimately intended them any harm, and they did not immediately respond to requests for comment.
They include Olli Heinonen, former deputy director general of the International Atomic Energy Agency (IAEA) for Safeguards, who worked on the Iran dossier for the UN nuclear watchdog.
Another is Giacomo Luciani, a prominent researcher on the political economy of energy in the Persian Gulf, who has played an important role in shaping EU-Persian Gulf energy relations.
Raheel Raza, a Canadian journalist of Pakistani origin, known for extensive activism against “Islamic terrorism,” was also scrutinized, along with Nadereh Chamlou, a former senior adviser at the World Bank and a non-resident senior fellow at the Atlantic Council.
Additionally, a Department 40 report described Iranian-Swedish dual national Reza Neshat, branding him “anti-system.”
One report from Department 40 reviewed by Iran International described the hacking of a non-Iranian citizen’s email accounts.
In it, the author describes emails found in the person's inbox and explains to senior officials how many of them involve Iranian or dual-national individuals and how those individuals could become new targets for scrutiny.
After gaining access to the person’s emails, they investigated their contacts and explored leads to identify subsequent targets.

Surveilling UK embassy, UN inspectors
Another report indicates Department 40 agents targeted medical centers in Turkey which are frequented by Israeli citizens traveling abroad for medical treatment.
The unit set up fake websites in Turkey that appeared to belong to Jewish associations or IT companies in order to eventually be able to abduct Israelis.
Reports also include details of operations and activities in 2021 in which agents describe “technical outfitting” for spying on diplomatic sites in Tehran – including the embassies of Oman, Switzerland and the United Arab Emirates.
The report also mentions drone footage of the British Embassy garden in Tehran and spying on IAEA inspectors in Iran.
Israel ambitions
The report also refers to Department 40’s efforts to carry out targeted assassinations inside Israel.
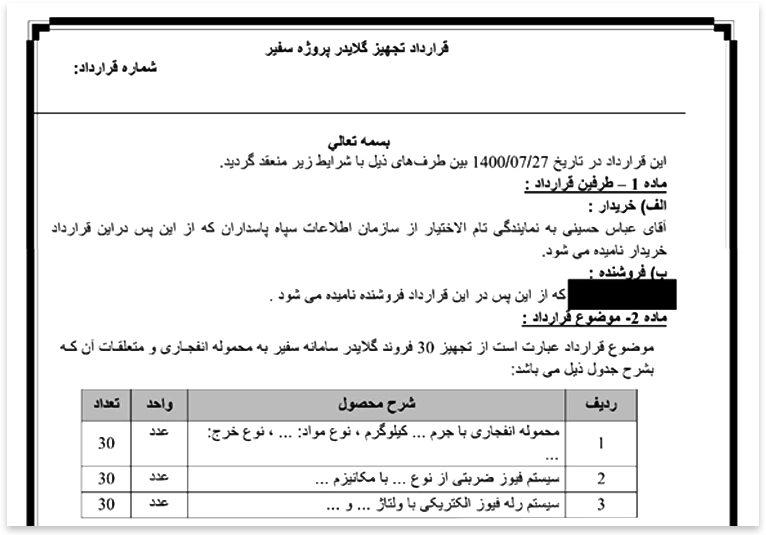
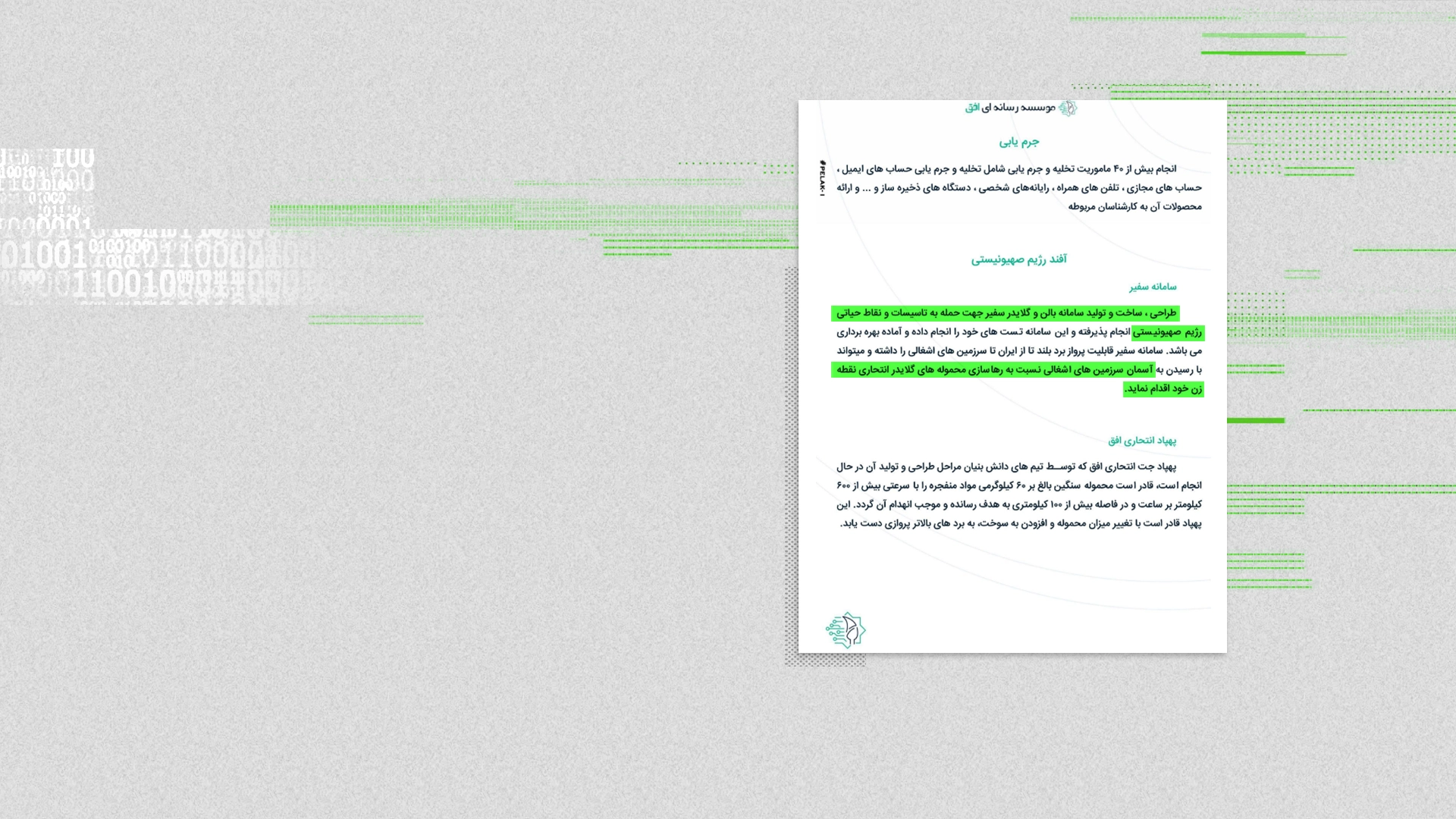
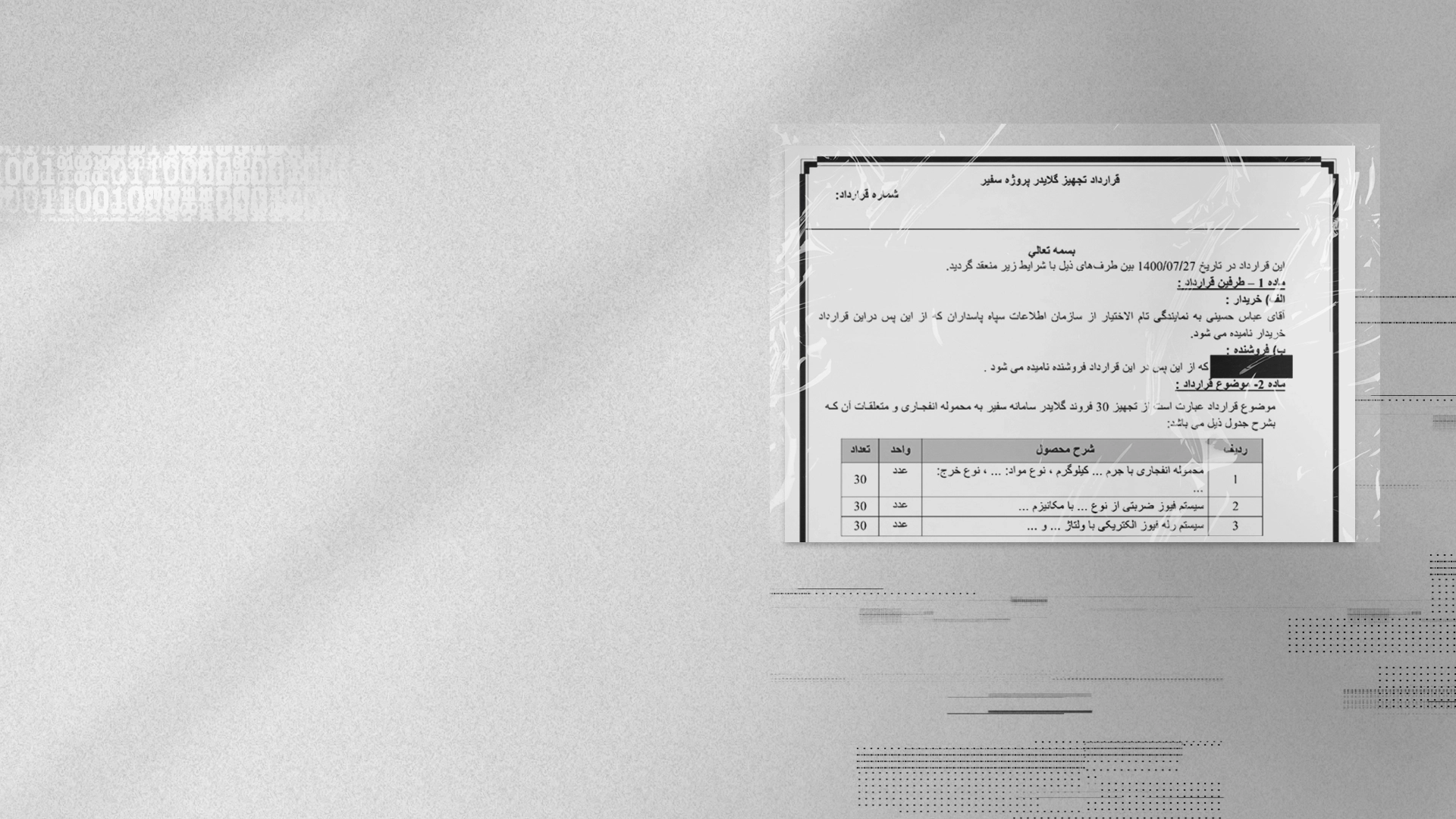
According to the document, the unit had an active project code-named Safir, or messenger, that aimed to design and use balloons and gliders capable of carrying and releasing explosives in “precision strikes” on Israeli soil.
Another Department 40 project, code-named Ofogh, or horizon aimed to manufacture a jet-powered suicide drone capable of carrying 60 kilograms of explosives to attack targets in Israel.
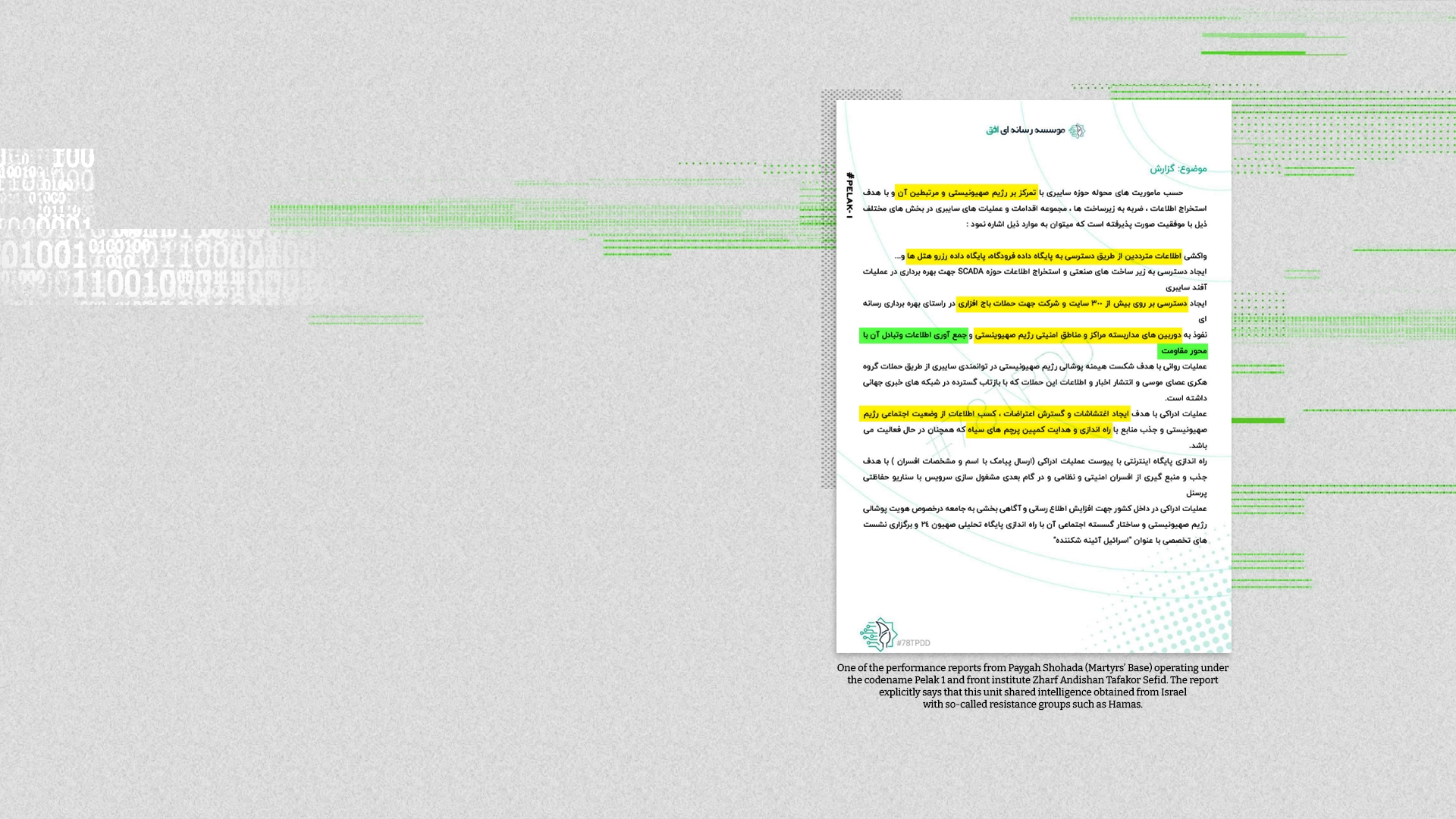
A report from 2022 indicated that information Department 40 had gathered from Israel had been shared with members of the “resistance”, Iran’s shorthand for Tehran-backed armed groups like Hamas in Gaza and Hezbollah in Lebanon.
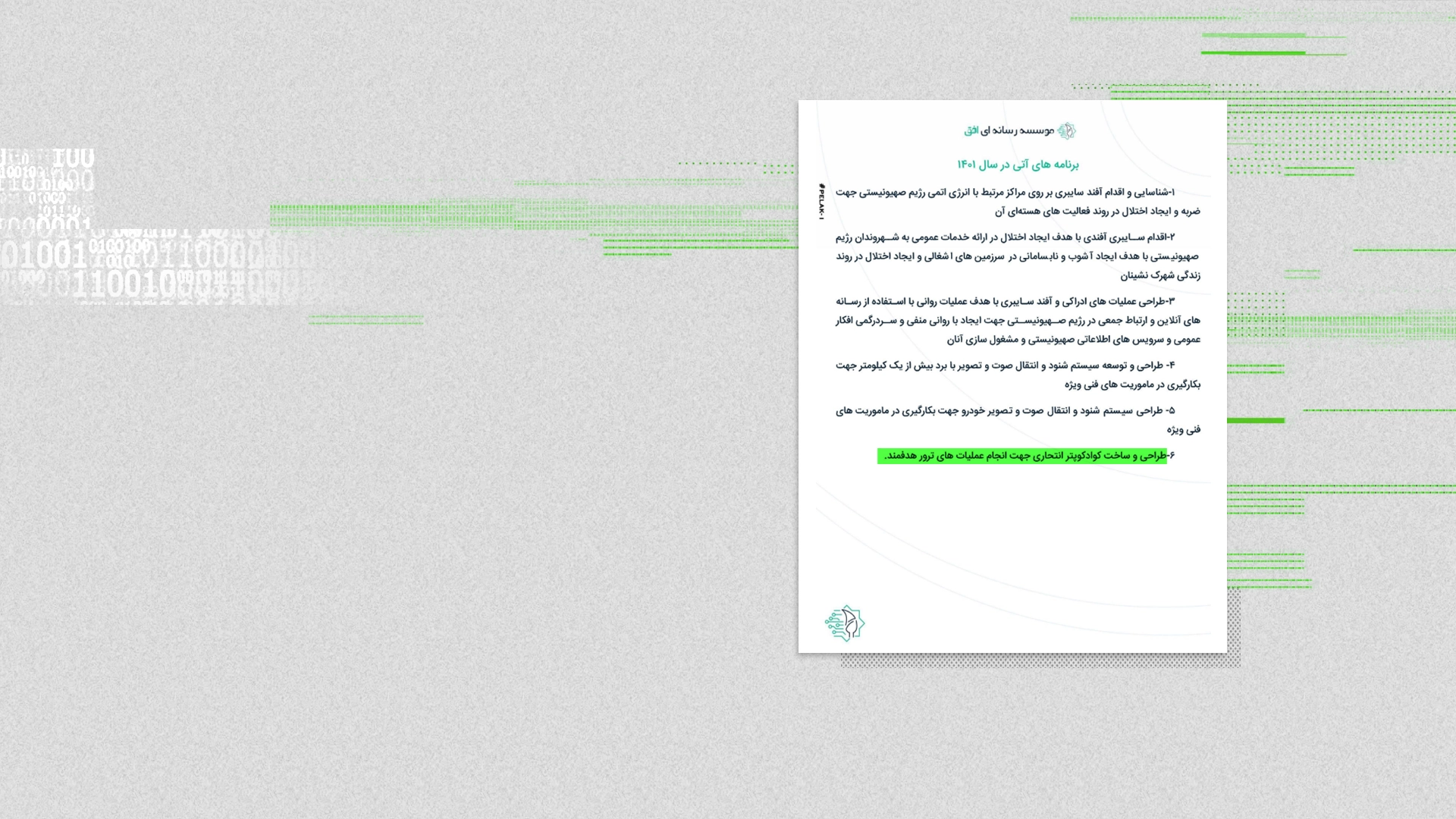
The unit lists among its priorities “designing and building suicide quadcopters for carrying out targeted assassination operations.”
Others included “identifying targets related to Israel’s nuclear activities, for offensive operations and disruption” and “designing cyber operations aimed at creating discontent and unrest in Israel and disrupting the lives of settlers.”
Surveilling UK embassy, UN inspectors
Another report indicates Department 40 agents targeted medical centers in Turkey which are frequented by Israeli citizens traveling abroad for medical treatment.
The unit set up fake websites in Turkey that appeared to belong to Jewish associations or IT companies in order to eventually be able to abduct Israelis.
Reports also include details of operations and activities in 2021 in which agents describe “technical outfitting” for spying on diplomatic sites in Tehran – including the embassies of Oman, Switzerland and the United Arab Emirates.
The report also mentions drone footage of the British Embassy garden in Tehran and spying on IAEA inspectors in Iran.
Israel ambitions
The report also refers to Department 40’s efforts to carry out targeted assassinations inside Israel.
According to the document, the unit had an active project code-named Safir, or messenger, that aimed to design and use balloons and gliders capable of carrying and releasing explosives in “precision strikes” on Israeli soil.
Another Department 40 project, code-named Ofogh, or horizon aimed to manufacture a jet-powered suicide drone capable of carrying 60 kilograms of explosives to attack targets in Israel.
A report from 2022 indicated that information Department 40 had gathered from Israel had been shared with members of the “resistance”, Iran’s shorthand for Tehran-backed armed groups like Hamas in Gaza and Hezbollah in Lebanon.
The unit lists among its priorities “designing and building suicide quadcopters for carrying out targeted assassination operations.”
Others included “identifying targets related to Israel’s nuclear activities, for offensive operations and disruption” and “designing cyber operations aimed at creating discontent and unrest in Israel and disrupting the lives of settlers.”

Origins of Department 40
The nucleus of what is now known as Department 40 emerged from a blog in the provincial city of Zanjan. The first discernible online activities of figures whom the documents link to the unit can be traced back to that website.
In April 2012, Department 40 chief Abbas Rahravi created a blog on an Iranian publishing service Blogfa titled the Zanjan Province Cyber Group.
The blog has since been removed, but archived content show that its authors followed the activities of the hacking group Ashiyaneh, or nest, one of the earliest hacker outfits linked to Iranian authorities.

Rahravi, born in Zanjan and now 33 years old, was recruited by IRGC Intelligence when he was about 20. After joining the organization, he was given the codename of Mikaeil Hosseini which was ultimately changed to Abbas Hosseini.
The Department’s ultimate activities were a far departure from the humble blog.
Materials reviewed by Iran International include a video of a drone test, as well as a contract for supplying equipment for the Safir explosive drone. Rahravi signed the contract under the alias Abbas Hosseini.
Rahravi appears to have been tasked with approaching companies to procure equipment needed for combat drones.

Rahravi, born in Zanjan and now 33 years old, was recruited by IRGC Intelligence when he was about 20. After joining the organization, he was given the codename of Mikaeil Hosseini which was ultimately changed to Abbas Hosseini.
The Department’s ultimate activities were a far departure from the humble blog.
Materials reviewed by Iran International include a video of a drone test, as well as a contract for supplying equipment for the Safir explosive drone. Rahravi signed the contract under the alias Abbas Hosseini.
Rahravi appears to have been tasked with approaching companies to procure equipment needed for combat drones.


Family ties, criminal records
For the first time, Iran International is publishing the names and details of Department 40 staff, revealing several family links among personnel.
The investigation shows that Leila Sharifi, a member of the Sisters unit, is the sister of Mehdi Sharifi, who leads Department 40’s hacking group. Narges and Atiyeh Naddafi, who work in the Sisters unit, are also sisters.
Several Department 40 employees have criminal records.
Senior manager Amirhossein Ahmadi Zonouz has a case involving the sale and possession of firearms. Vahid Molavi, from the Karaj hacking unit, has military court cases related to money laundering and abuse of power.
In the case files of Omid Fallah, a member of the “Brothers” unit, there are charges relating to alcohol consumption, involvement in fights and insulting and threatening fellow citizens.
A review of how these cases were handled shows that in some instances the defendants were acquitted, though details are incomplete.